penetration test
Categories: security service,Solution
penetration test
Penetration testing is a process in which, with client authorization, supervision, and without interfering with the normal operation of the target system, engineers use manual andsuretyDetection tools, simulating hacker attack methods on the target system's technical weaknesses, defects or vulnerabilities to carry out controlled non-destructive attack testing, and provide penetration test reports, so that customers can clearly know the security risks existing in the target system.
Penetration Testing Classification
-black box test
penetration testThe engineer tests the system without knowing anything about the target system. All information about the system is collected by the engineers themselves through penetration testing.
-gray box testing
Penetration test engineers can request some of the information from the subject through normal channels, includingreticulationTopology, employee information, and even some of the site's users/passwords.
-internal testing
Testers access the organization's intranet directly to test the information system from within the organization's network, which involves crossing the boundaries of the internal network, simulating an attack scenario in which an internal host has been compromised as a springboard for an intrusion or initiated by an internal violator.
-External testing
Testers use the Internet to test the information system from outside the organization's network through the organization's open information services, and the testing process involves the security of each link in the information system access channel from the network entrance to the information system application layer procedures, simulating the scenario of an external intruder attempting to invade the organization.
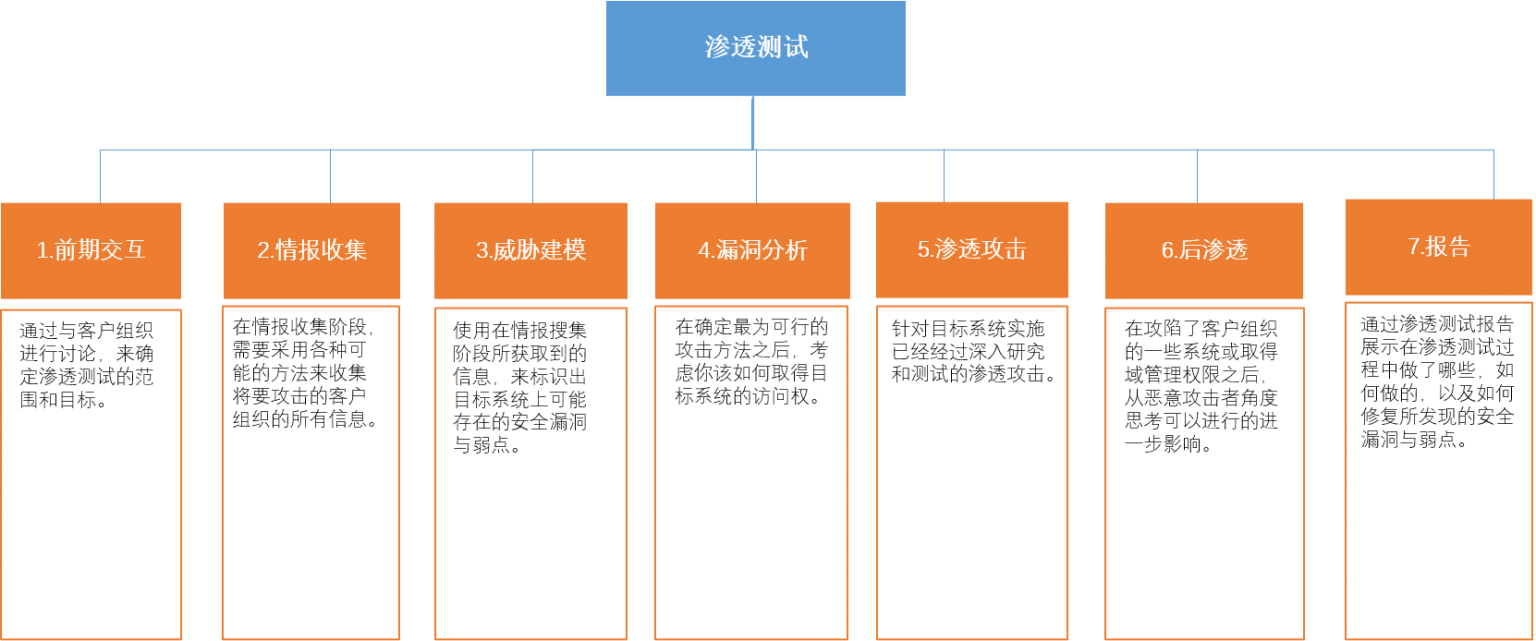
permeabilityTest reference standards(PTES)
Currently widely recognized in the security industry, the Penetration Test Execution Standard defines the process and phases of a true penetration test, ensuring that a penetration test can be conducted in a standardized manner. The standard divides the penetration testing process into seven phases and defines different processes and extensions within each phase.
Service Introduction
Qixing penetration testing product is a product of Qixing cloud congregation.credible technologyThe Center launched by the senior security experts proficient in penetration testing technology, within the scope of customer authorization, with reference to PTES (penetration testing execution standard) on customer information systems to simulate hacking attacks on commercial testing services, used to help customers assess the current security of information systems. We provide a variety of testing methods including extranet penetration testing, intranet penetration testing, black-box testing, gray-box testing, etc., covering websites/web applications included in the information system,server (computer), databases, middleware, network equipment, terminals and other related hardware and software assets.
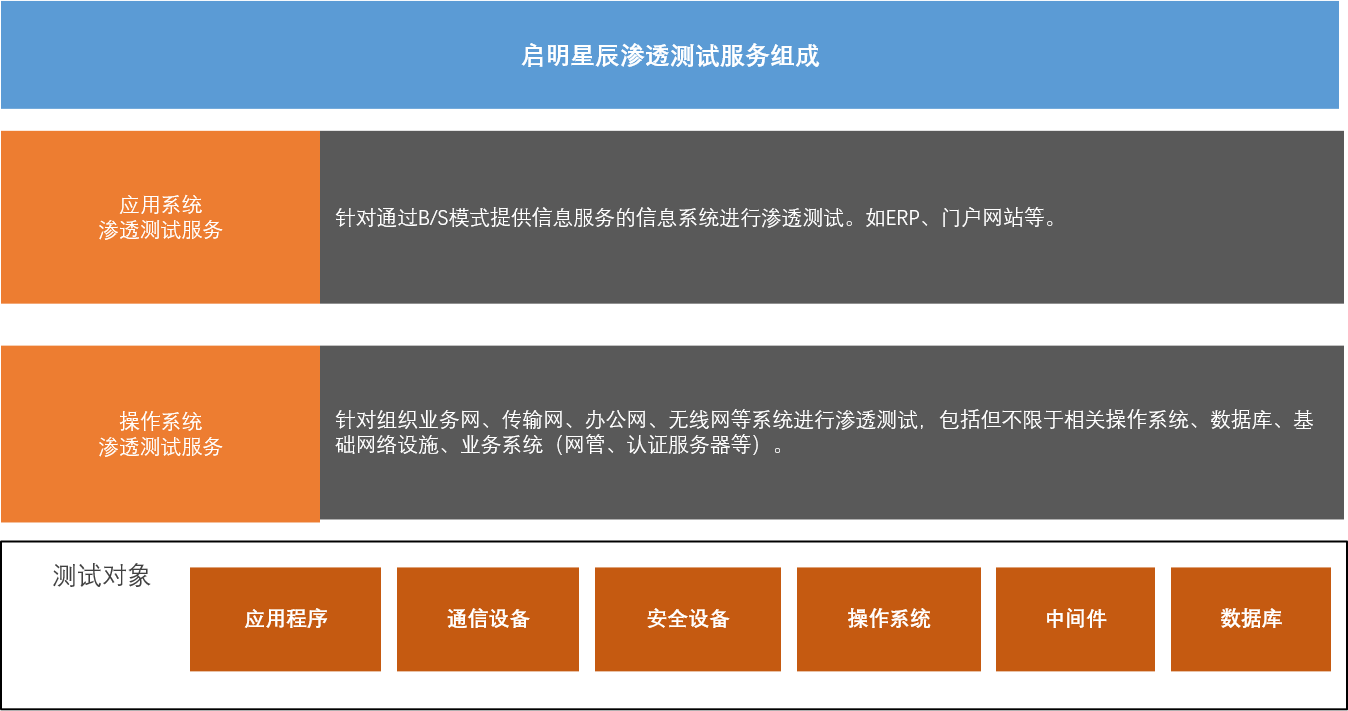
Service Components
Service Specifications
Application penetration testing
For organizations wishing to test a website or other B/S business system for security vulnerabilities that can be exploited by hackers. Test engineers, remotely or on-site, conduct various vulnerability tests on all environments related to the operation of the system (including but not limited to security devices, network devices, servers, middleware, databases, web applications) within the scope of authorization, with the perspective of a fully simulated hacker.
System penetration testing
Aiming at the services provided for testing whether there are security vulnerabilities that can be exploited by hackers in the basic network environment of the organization's business network, core network, transmission network, office network, wireless network, and so on. Test engineers, by accessing the customer's network, conduct various vulnerability exploitation tests on all network communication-related equipment (network equipment, security equipment, wireless APs, terminals) and network-related business systems (network management systems, authentication systems) within the authorized scope from the perspective of a hacker.
















