vulnerability scan
Categories: security service,Solution
Vulnerability Scanning Solutions
Products
Vulnerability scanning by skyglassand management system is a vulnerability scanning product independently developed by Qixingchen and based on thereticulationVulnerability analysis, assessment and management system. Provides vulnerability checking, assessment and management of hosts, operating systems and network devices.
Functional Features
Technical Advantages
- All-in-one vulnerability scanning system integrates system leakage scanning, web leakage scanning, and configuration verification to facilitate users to assess the security of the system from multiple dimensions.
- Rich Vulnerability Knowledge Base The number of vulnerabilities exceeds 45,000, supporting the scanning of cloud platform classes, website open source architecture classes, Apple classes, and so on.
- Multi-factor quantitative risk assessment algorithm based on the international vulnerability common scoring standard CVSS and asset level and importance of the "multi-factor quantitative risk assessment" algorithm, can quantitatively assess the security risk of the target host and network.
typical application
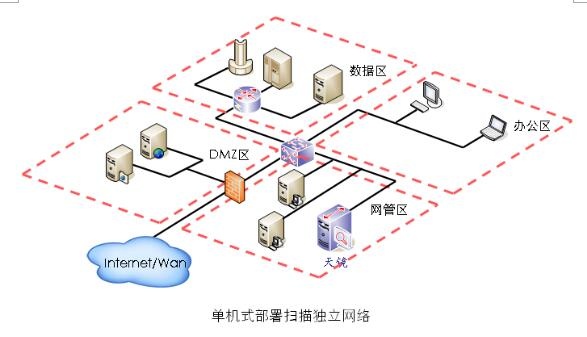
Stand-alone deployment approach
Small and medium-sized enterprises and organizations can achieve independent vulnerability scanning of various regions of the entire network by deploying a single-stage Sky Mirror scanning unit, the deployment of which is shown in the figure below. This independent vulnerability scanning scenario is also suitable for monitoring and evaluation organizations, who can install Sky Mirror in thenotebookslaptopsThe mobile inspection and evaluation of independent network units can be realized.
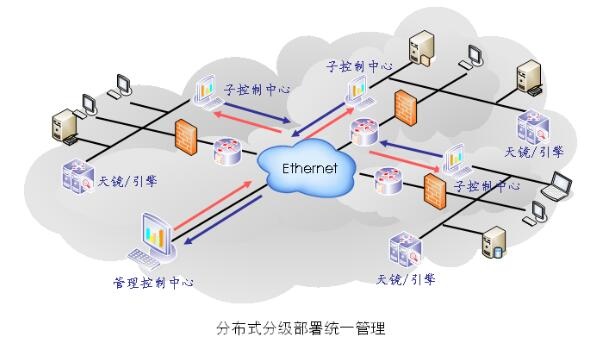
Multi-level deployment approach
Multi-level deployment of vulnerability scanning and management system is suitable for large-scale information systems, in addition to reducing human resources investment, but also able to implement a unified scanning strategy for the entire network vulnerability management and effective supervision, reducing the cost of communication between the upper and lower levels, and improving the efficiency of vulnerability scanning and management work.