Equalization compliance
Categories: security service,Solution
Equalization Compliance Building Program
The company's level protection construction and rectification is based on the requirements of national level protection related policies and standards, combined with the actual situation of the customer's organizational structure, business requirements, etc., and through a set of standardized level protection project construction and rectification process, to assist the customer to complete the level protection construction and rectification work, and to achieve the goal of compliance engineering and construction.
Business Advantages
firmsGrade protection constructionThe main advantages of, rectification are reflected in:
☆ Level protection expert group member units
☆ Participant in the development of standards and norms for level protection
☆ Leading practitioner in providing total level protection construction projects
☆ good and powerfulinformation securityService Qualification
☆ Successful project experience in large-scale national level protection
☆ AbundancesuretyIntegration project experience and hierarchical protection technology accumulation
☆ Specialized security services team
☆ High-quality solutions for full-coverage security products
☆ Mature system integration team, service and engineering quality assurance
☆ Business-centered and demand-driven
Various industries and units that need to be constructed and rectified in accordance with the standards and specifications for level protection protection.
The main contents of the company's hierarchical protection construction and rectification business include the following:
☆ Security Planning: According to the national level protection related requirements, combined with the customer's organizational structure, business requirements, the actual situation, collate the customer's actual needs and objectives of security construction work, the formation of the "Research Report" and the "Overall Planning";
☆ Classification filing: Determine the scope of the client's classification, analyze the client's organizational structure, business requirements and other contents, conduct mapping survey to determine the target of classification; for the target of classification, based on the national "Classification Guidelines" to assist the competent authorities of the system in the preliminary determination of the level of the system, and to form the "Classification Report"; assist in the expert review and approval, and assist in the completion of the classification filing work;
☆ risk assessment: Through asset assessments, vulnerability scans, and audits,reticulationArchitecture analysis, data flow analysis, etc., for the client to comprehensively analyze the current status of the information system's assets, hosts, databases, security equipment, network weaknesses, threats and risks, and form a "Risk Assessment Report" (optional value-added services);
☆ Gap Analysis: In accordance with the security requirements of the corresponding level of hierarchical protection, the system to be constructed is subjected to gap analysis of the security system and other aspects, and a Gap Analysis Report is formed;
☆ Security construction: according to the confirmed level of protection gap report analysis of the situation, the development of the overall "solution", to assist in program evaluation, to assist in the implementation of the implementation of level of protection security construction work;
☆ Rectification and Reinforcement: According to the corresponding requirements corresponding to the corresponding level of protection, formulate the required security management system, processes and forms, technical standards and norms and other documents, and formulate a reinforcement program for hosts, network equipment and databases, and reasonably strengthen the security of the equipment through patching, modifying security configurations, adding security mechanisms and other methods to meet the requirements of the level;
☆ Auxiliary assessment: In order to better assist customers to pass the level protection assessment work, provide auxiliary assessment support;
Scope of Services
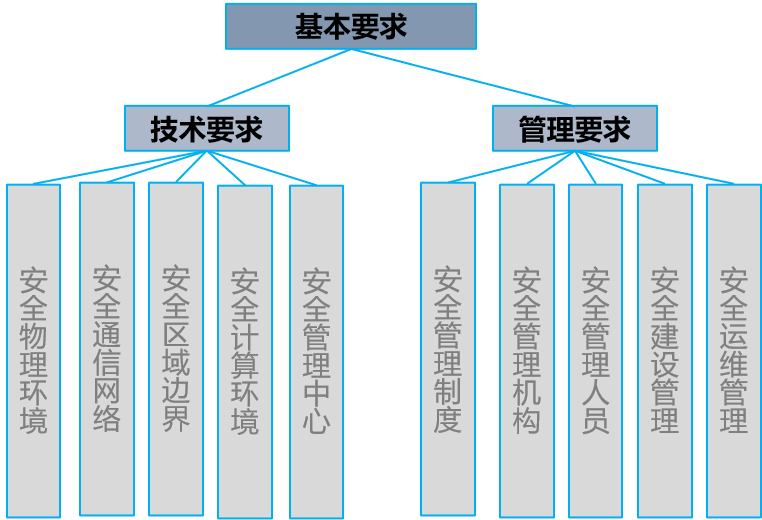
QPCC Level Protection Compliance Consulting Service Version 2.0 is divided into technical and management aspects, just like Version 1.0.
The technology includes, security physical environment, security communication network, security area boundary, security computing environment, security management center five aspects;
Management includes five aspects: security management system, security management organization, security management personnel, security construction management, security operation and maintenance management
Implementation process
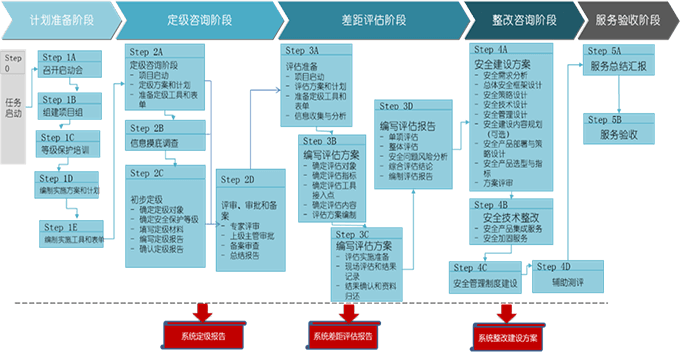
The implementation process of Qixingchen level protection compliance consulting service includes five stages: plan preparation stage, classification consulting stage, gap assessment stage, rectification consulting stage, and service acceptance stage with five stage steps, as shown in the figure below:
Functional specifications
| service module | Services | Service approach/unit (of measure) | Deliverables |
| Star-Level Protection Classification Consulting | According to the national information security level protection related standards, document requirements and industry grading requirements, assist in system grading, prepare grading reports (by system), formulate system grading reports according to the "Information Security Level Protection Filing Implementation Rules", prepare filing forms and complete the filing. | On-site or remote/person-day | Information System Security Level Protection Classification Report Information System Classification Expert Review Report Information System Classification Audit Form for Classification by Higher Authority of Information System Filing Form |
| Star-Class Protection Gap Assessment Service | Based on the requirements of the national information security level protection related standards and documents, combined with the security protection level of the customer's information system, the security assessment of the information system security level protection status, the examination and evaluation of the information security control capability, and the process of determining whether the information system security protection capability meets the basic requirements of the corresponding level, in order to help the customer to timely discover the information security risks. | On-site or remote/person-day | Gap Assessment Record Sheet - Set Comprehensive Calculation Sheet xx System Level Protection Gap Assessment Report |
| Star-Level Protection Rectification Consulting Service | According to the results of grading and level gap assessment, carry out overall analysis, analyze the user's security needs, based on the national information security level protection related standards and document requirements, meet the customer's security needs at the technical and management levels on the premise of security planning and design; according to the rectification design plan, carry out technical rectification (security product integration, security reinforcement), management rectification, so as to meet the requirements of the level of protection We also assist customers in completing level protection assessment. | On-site or remote/person-day | Network Security Level Protection (General Security Requirements) Construction Program Network Security Level Protection (General Security Requirements) Construction Programcloud computing(Security Extension Requirements) Construction Program" "Expert Evaluation Opinion Sheet for Class Protection Security Construction Program" "Security Management System" Full version (with checklist) and simplified version |
Service Features