DeepService Firewall Next-Generation Firewall AF
Product Overview
Deepsign Firewall Next Generation Firewall AFSpecialization required for fusion of borders against threatssuretyCapabilities are delivered in a simple and easy-to-use way to provide comprehensive protection against all types of threats, with multiple intelligent models and smart linkage means to continuously combat the emerging new risks.
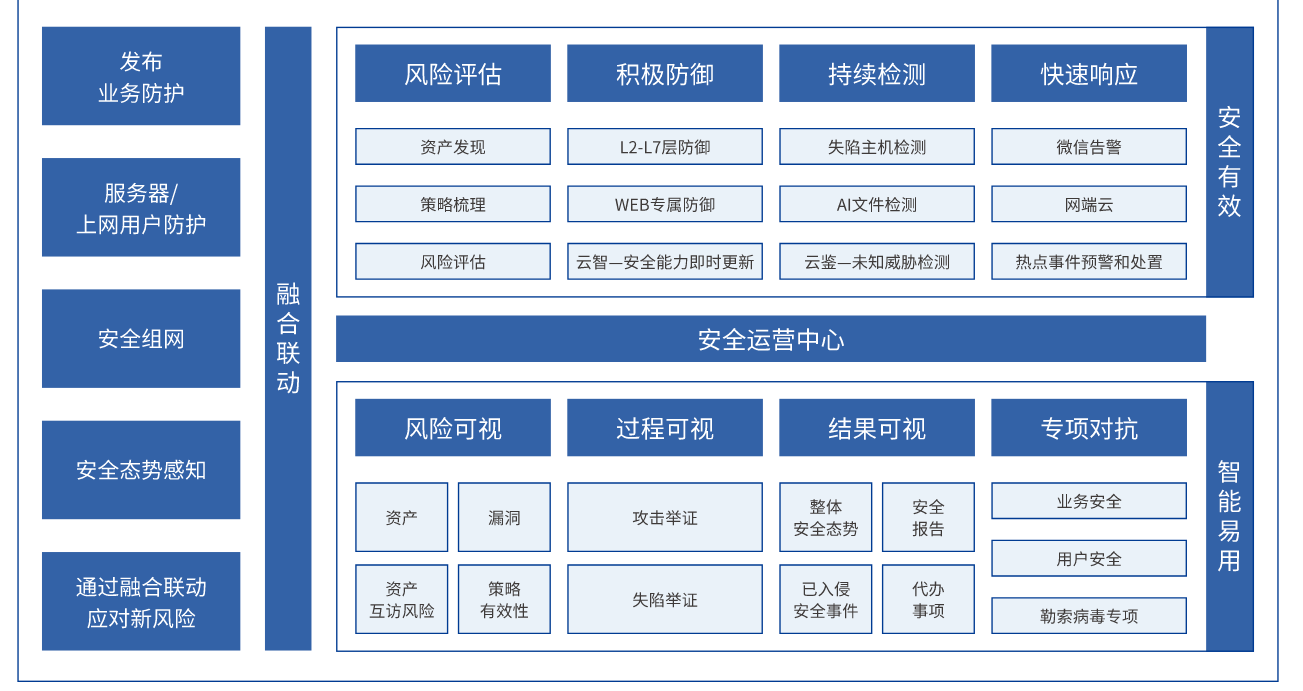
Full protection
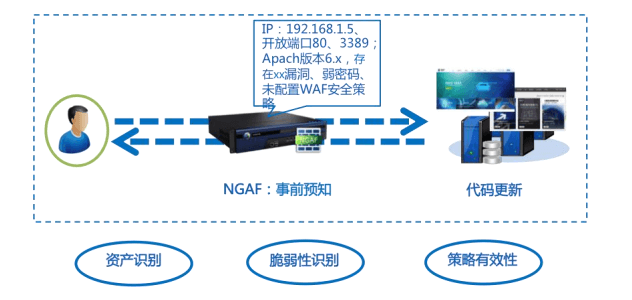
2.1.1 Prior knowledge: assets/vulnerabilities/strategy effectiveness
DeepService NGAF enables the prior management of internalserver (computer)It also automatically recognizes the server on which the
It is also possible to determine whether the identified assets have corresponding security protection policies, such as vulnerabilities and weak passwords.
and whether it is in force.
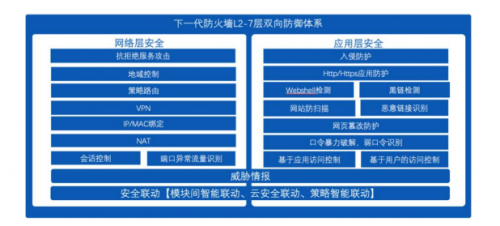
2.1.2 Defense-in-action: complete defense system + security linkage + threat intelligence
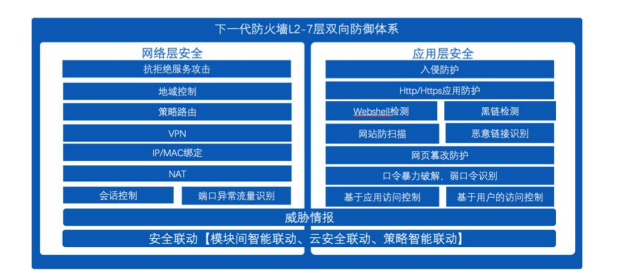
DeepTrust NGAF integrates a variety of security technologies at the incident defense level, providing a complete security defense system with L2-7 layers.
Ensure that there are no shortcomings in security protection, but also through the security linkage function to strengthen the timeliness and effectiveness of the defense system, package
These include inter-module linkage blocking, linkage with cloud security, and intelligent linkage of policies. In addition, NGAF also has a wide range of
Developing third-party security agency cooperation throughNational Vulnerabilitiesinformation repository, Google Virustotal malicious link repository, and other sources.
The input of coercive intelligence helps users to be able to prepare their defenses well in advance of security outbreaks.
2.1.3 Ex Post Detection & Response: Continuous Detection of Threat Behavior & Rapid Response
Traditional security construction mainly focuses on border security defense, and lacks the ability to detect and respond to the bypassing of security defense measures.
The impact of a security incident can be greatly minimized with good post-event detection and response measures. DeepTrust
NGAF combines after-the-fact detection and rapid response technology to help users find out what's going on, even after a hacker has breached the system.
Detecting malicious behavior after an attack, such as detecting malicious behavior initiated by bot hosts, web page tampering, website black link implantation and website
Webshell backdoor detection, etc., and quickly push alert events to assist users in responding to dispositions.
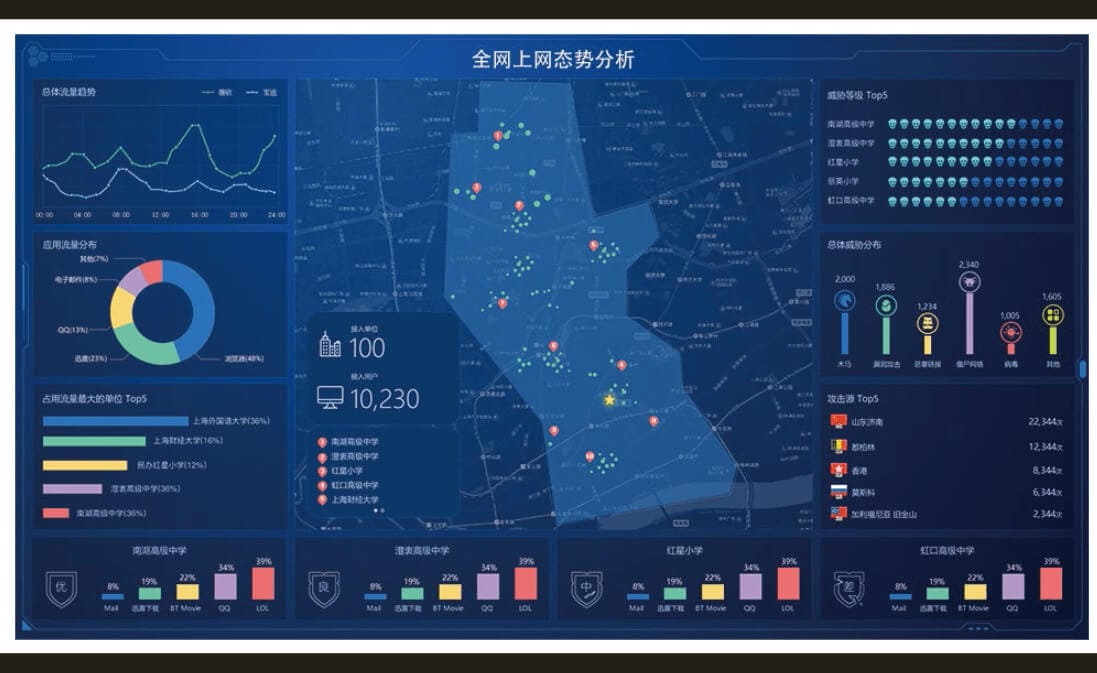
full visualization
2.2.1 Prior knowledge of security risks
Clear Understanding of Asset Vulnerability
Quickly discover strategy effectiveness
2.2.2 Perceptions of the protection process during the event
Attack events match different attack phases
2.2.3 Ex post facto perceptions of protection outcomes
Demonstration of the current state of security based on the information asset dimension
Consolidated Risk Statement
Introduction to the main features:
| sports event | norm | Specific functional requirements |
| Deployment method | Deployment model | Supports routing, transparent, bypass, virtual wire, and hybrid deployment modes; |
| real time monitoring | Equipment Resource Information | Provides device real-time CPU, memory, disk occupancy, number of sessions, number of online users, and system time,reticulationinterfaces and other information; |
| security status | Provide security event information, including recent security events, server security events, terminal security events, etc. The event information provides the occurrence of the event, source IP, destination IP, type of attack, and URL of the attack; | |
| flow state | Provides real-time user traffic ranking, application traffic ranking, all line application flow trends, traffic management status, and connection monitoring information; | |
| strategy linkage | Provides source IPs for real-time intelligent inter-module linkage blocking to enable dynamic intelligent security management; | |
| network protocol | internet service | Support ARP proxy, static ARP binding, ARP spoofing protection, configure DNS and DNS proxy, support DHCP relay, DHCP server, DHCP client; support SNMP v1, v2, v3, support SNMP Trap; |
| routing service | Supports static routing, RIP v1/2, OSPF, and policy routing; | |
| Port Characteristics | Supports link probing, port aggregation, and interface linkage; | |
| Firewall/VPNfunctionality | Packet Filtering and Stateful Inspection | Can provide static packet filtering and dynamic packet filtering. Supported application layer packet filtering, including: application layer protocols: FTP, HTTP, SMTP, RTSP, H.323 (Q.931, H.245, RTP/RTCP), SQLNET, MMS, PPTP, etc.; transport layer protocols: TCP, UDP |
| NAT Function | Supports mapping of multiple internal addresses to the same public address, mapping of multiple internal addresses to multiple public addresses, one-to-one mapping of internal addresses to public addresses, simultaneous translation of source and destination addresses, access to internal servers by external network hosts, and support for DNS mapping. Configurable validity time for address translation support Supports multiple NAT ALGs, including DNS, FTP, H.323, SIP, etc. | |
| Attack resistance | Supports defense against Land, Smurf, Fraggle, WinNuke, Ping of Death, Tear Drop, IP Spoofing, CC, SYN Flood, ICMP Flood, UDP Flood, DNS Query Flood, ARP Spoofing Attack Prevention, ARP Active Reverse Lookup, TCP message flag bit illegitimate attack prevention, support IP SYN speed limit, oversized ICMP message attack prevention, address/port scanning prevention, DoS/DDoS attack prevention, ICMP redirection or unreachable message control, etc. In addition, it also supports static and dynamic blacklisting function, MAC and IP binding function. | |
| IPSec VPN Features | Support AES, DES, 3DES, MD5, SHA1, DH, RC4 and other algorithms, and support for the expansion of the State Secrets Office SCB2 and other encryption algorithms to support MD5 and SHA-1 verification algorithms; support for a variety of NAT network environment of the VPN network; support for third-party standard IPSec VPN for docking; * headquarters and branches of the number of routes, can be carried out one by one between the lines. IPSecVPN tunnel establishment, and set up the main tunnel and backup tunnel, the main tunnel can be bandwidth stacking, average distribution of traffic by packet or session, the main tunnel disconnected backup tunnel automatically enabled to ensure that the IPSecVPN connection will not be interrupted; you can set up a different multi-line policy for each branch individually; single-arm deployments also support multi-line policy; | |
| SSL VPN Features | Support SSL VPN remote access; | |
| Application Access Control Policy | application identification | Support for more than 1,000 kinds of applications, more than 2,500 kinds of application actions, can identify P2P, IM, OA office applications, database applications, ERP applications, software upgrade applications, Trojan horse outreach, speculation software, video applications, proxy software, Internet banking and other protocols; support for customization of the rules. |
| Application Access Policy | Provides application access control list formulation based on application identification type, user name, interface, security domain, IP address, port, and time. | |
| APT testing | Botnet Feature Library | Built-in library of over 200,000 viruses, Trojans, spyware, and other malware signatures, and constantly updating the signature content; |
| Cloud Security Detection | Supports the realization of virtual sandbox dynamic detection technology through the security cloud. It can detect the modification of registry, file system, etc. by unknown threats in the sandbox, and quickly update it to the equipment of each node through cloud linkage, which can realize rapid and unified protection against unknown attacks; | |
| Abnormal connection detection | It can effectively distinguish dangerous traffic among common application traffic on WEB servers such as RDP, SSH, IMAP, SMTP, POP3, FTP, DNS, HTTP, etc., and also provide early warning for regular applications running on non-standard ports; | |
| Outgoing traffic anomalies | Capable of detecting DDoS behaviors initiated by intranet broilers, such as ICMP, UDP, SYN, and DNS outgoing request anomalies; | |
| IPS Intrusion Prevention | Type of protection attack | Including worm / Trojan / backdoor / DoS / DDoS attack detection / scanning / spyware / exploit attacks / buffer overflow attacks / protocol anomalies / IPS escape attacks, etc. |
| Password Breach Protection | Supports password brute force protection for common application servers and database software (e.g. HTTP, FTP, SSH, SMTP, IMAP, MySQL, Oracle, MSSQL, etc.); | |
| Classification of protection objects | Vulnerabilities are categorized into server protection and client protection, and are also classified into security boundaries such as "high", "medium", "low", and so on. | |
| Vulnerability Description | Vulnerability details display: vulnerability ID, vulnerability name, vulnerability description, attack object, danger level, reference information, address and other content for easy maintenance | |
| strategy development | IPS policies can be configured based on source area, destination area, and destination IP group, and the destination IP group supports multi-selection. | |
| Number of feature libraries | Attack signature library: 3500+ and can be upgraded automatically or manually. | |
| anti-avoidance | Support TCP protocol disorder retransmission, TCP packetization | |
| Processing Action | Supports automatic interception, logging, and uploading gray-scale threats to the "cloud". | |
| Server Protection | Web Attack Protection | Protect servers from web application based attacks such as SQL injection protection, XSS attack protection, CSRF attack protection, Webshell script uploads, system command injections, file containment attacks, directory traversal attacks, information leakage attacks, and web content management system vulnerability protection; |
| Parameter protection | Provides both active defense and custom parameter protection. Active defense forms a parameter whitelist through self-learning to block abnormal parameter content, while custom parameters provide more customized parameter protection; | |
| Application hiding | Support HTTP and FTP service hiding, can be filtered for HTTP response header and HTTP error page, Web response header can be customized to hide the software version information returned by the FTP server; | |
| weak password protection | Supports FTP weak password protection, Web login weak password protection, Web login plaintext transmission detection; | |
| privilege control | Support file upload server filtering, support blacklisting of specified URLs, add exclude URL directory feature | |
| strategy development | Configuration Options:You can set the source, destination area, destination IP and port number, port number supports setting the port number for web application, FTP, mysql, telnet, ssh services | |
| Login Protection | User login privilege protection, support page two-factor authentication method, strengthen the sensitive page access privilege control; | |
| HTTP Anomaly Detection | Detect HTTP protocol anomalies and filter for HTTP GET, POST, HEAD, OPTIONS, PUT, DELETE, TRACE, SEARCH, CONNECT, LOCK, UNLOCK and other methods; | |
| CC Attack Protection | Supports HTTP protocol CC attack protection, which is controlled according to the source IP request threshold; | |
| Website Scanning Protection | Prevents web servers from being scanned for vulnerabilities by common scanners; | |
| Buffer overflow detection | Support for URL overflow detection , POST entity overflow detection and HTTP header fields overflow detection ; | |
| Https protection | Supports decryption of Https and content inspection, requires importing server certificates; | |
| Sensitive information leakage prevention | Sensitive Information Protection | Built-in ID card, MD5, cell phone number, bank card number, mailbox and other sensitive information types, support for customizing the content of sensitive information; support for statistics in two ways: IP and connection; |
| File Download Filtering | Filtering of outgoing sensitive documents by defining sensitive information file suffixes; | |
| exclude from whitelisting | Support whitelist exclusion list, for the IP in the whitelist, the URL is not detected; | |
| Service risk analysis | open port scanning | Built-in common services such as http, https, ftp, tftp, pop3, smtp, imap, telnet, ssh, vnc, oracle, mssql, mysql, netbios, dns, rdp, etc. open port list, and support for customizing the need to scan the server ports; |
| Vulnerability Risk Analysis | Through the scanning and detection of open ports, we further analyze the underlying vulnerability threats that may exist in the open ports; | |
| Weak password scanning | Supports weak password scanning for ftp, mysql, mssql, oracle, netbios, ssh, rdp, vnc and several application services. | |
| One-click protection | For the detected open ports, server vulnerability information, weak password threats, can be one-click automatically generate the appropriate protection policy, simplify the user's operation and maintenance management. | |
| Risk scanning report | For the scanned risk content supports export in pdf format; | |
| Web Vulnerability Scanning | Web Scanner | Support SQL injection, SQL blind injection, cross-site scripting attacks (XSS), cross-site request forgery (CSRF), operating system commands, local file containment, remote file containment, brute force cracking, weak password login, XPATH injection, LDAP injection, server-side containment (SSI), and so on, rich in Web application service vulnerability detection; |
| Vulnerability Reporting | Support for exporting Web vulnerability analysis reports in HTML format; | |
| Real-time vulnerability analysis | Real-time vulnerability risk | Supports passive analysis of traffic passing through the device, the analysis includes underlying software vulnerability analysis, Web application risk analysis, Web insecurity configuration detection and server weak password detection, and real-time generation of analysis reports. |
| black-chain detection | Ability to detect black links inserted in website pages; | |
| Real-time vulnerability analysis and identification library | Separate feature identification libraries for server security risks and potential threats; | |
| Threat intelligence warning and disposal | threat intelligence | With the threat intelligence function, can actively push the current popular 0 day or high-risk vulnerabilities, and can provide vulnerability detection tools to carry out scanning self-check of the business, and can be based on the scanning results of the one-click generation of security protection policies; |
| Website tampering protection (plug-in version) | Client detection method | After the client plug-in is installed on the server, IRF file-driven streaming technology is used to configure the file directory to be protected and the applications that are allowed to modify the directory through the plug-in, and to identify whether the application that modifies the directory of the protected web site is legal or not; The client plug-in supports logging of attempts to modify, delete, and add files in the protected directory; Client plug-ins need to protect their own security, including the background process is not allowed to be forced to suspend, access to the client plug-in management page requires password authentication, access to the client plug-in management page needs to have an automatic timeout mechanism; |
| Website Backend Login Management | Support in the gateway device settings on the CMS way to log in to the site management backstage for e-mail secondary authentication; Support in the gateway device settings on the FTP way to log in the site management background for the second authentication by mail; Supports setting up a whitelist for website back-end login management. Users in the whitelist do not need to be authenticated twice to log in to the website management back-end; | |
| virus protection | virus engine | Based on the stream engine checking technology, it can check and kill HTTP, FTP, SMTP, POP3 and other protocols. |
| Type of protection | It can check and kill a large number of file-type, network-type and mixed-type viruses in real time. It also adopts a new generation of virtual shelling and behavioral judgment technology to accurately check and kill all kinds of virus variants and unknown viruses. | |
| Number of virus libraries | Supports more than 100,000 virus databases, and can be automatically or manually upgraded | |
| Processing Action | Actions after detecting a virus: support logging, blocking connections | |
| WEB FILTERING | URL Filtering | Filter user web behavior to protect users from attacks; support only filter HTTP GET, HTTP POST, HTTPS and other application behaviors; and block and record logs |
| File Type Filtering | Supports file filtering for uploads, downloads and other operations; supports customized file types for filtering; supports schedule-based policy formulation; supported processing actions include: blocking and logging | |
| traffic management | virtual multiline | Supports one physical line to be virtualized into multiple virtual lines, and flow control can be performed on multiple virtual lines respectively; |
| Type of flow control | Supports bandwidth division and allocation based on application type, website type, and file type; | |
| Control granularity | Supports bandwidth division and allocation policy based on time period; supports the realization of bandwidth division and allocation based on the target IP of access behavior; | |
| user management | local certification | Supports triggered WEB authentication, static username and password authentication, etc; |
| Third Party Certification | Supports third-party authentication such as LDAP, Radius, POP3, and Proxy; | |
| IP, MAC authentication | Supports IP authentication, MAC authentication, and IP/MAC binding authentication; | |
| New User Authentication | Implemented based on the source IP segment of the new user: | |
| 1. Rules for the creation of differentiated accounts for new users; | ||
| 2. Differentiated automatic grouping rules for new users; | ||
| 3. Differentiated authentication rules for new users; | ||
| 4. Differentiated IP and MAC binding rules for new users; | ||
| Public accounts | Supports multiple people logging in with the same account, and supports duplicate login detection mechanism; | |
| Account validity | Designated accounts support expiration limits and automatic expiration; | |
| single sign-on | Support AD, POP3, Proxy single sign-on, simplify user operation; | |
| It is possible to force users of specified users and specified IP segments to use single sign-on; | ||
| Mandatory AD certification | The specified user must log on to the operating system with an AD domain account, otherwise Internet access is disabled; | |
| authentication failure | Supports a basic network access rights mechanism for users who fail authentication; | |
| jump to a new page | Page jumps are supported for successfully authenticated users: | |
| 1. Jump to the URL address originally entered by the user; | ||
| 2. Jump to the URL address specified by the administrator; | ||
| 3. Jump to the page ranking the user's Internet access information; | ||
| 4. Jump to the logout page. | ||
| Post-accreditation Announcement | Supports displaying specified web pages to authenticated users; | |
| Account Import | Supports importing from local and scanning import, and importing account/group/IP/MAC/description/password information as text; | |
| Supports importing account and group information from an LDAP server; | ||
| Organizational structure | User grouping supports tree structure, parent group, child group, set of groups within a group and so on; | |
| User status query | Support user login and logout history query, including display of Internet traffic | |
| Gateway Management | Administrator account | Support administrator privilege hierarchy, divided into security administrators, auditors and system administrators, security administrators are only allowed to view and edit security policies and security logs by default; auditors are only open by default.data centerLog viewing and editing privileges, not device management privileges; system administrators by default have system management privileges other than security functions, not device log viewing privileges; |
| management interface | Support SSL encrypted WEB way to manage the device; support email, SMS (expandable) and other alarm methods; | |
| Alarm Management | Administrator logins, viruses, IPS, web attacks, and logs are available.stockpileAlarm settings such as insufficient space; | |
| Troubleshooting Tools | Provides graphical troubleshooting tools for administrators to troubleshoot policy errors and other faults; | |
| Configuration Wizard | Provides configuration guidance for routing, bridge, bypass and other deployment modes, and provides configuration guidance for gateway application scenarios such as protecting servers, protecting the safety of intranet users' access to the Internet, guaranteeing intranet users' access to the Internet bandwidth, and guaranteeing timely alerts and retaining evidence of attacks to simplify the administrator's configuration; | |
| high availability | HA | Supports A/A, A/S mode deployment, session synchronization, configuration synchronization and user information synchronization; |
| data separation | Support operating system and data read/write separation, the system runs on the CF card media, log read/write operations on the hard disk. (This configuration is default for devices above 6020, the following models need to be customized) | |
| Logs and Reports | data center | The appliance must support both a built-in data center and a standalone external data center; the standalone external data center must have MySQL built-in, eliminating the need to install other databases separately; The external data center supports network-wide security monitoring, which can display the security status of all branch devices, summarize the security logs, and see the risk level of the network-wide security devices, server security, user security and the source of attacks, as well as attack trends; |
| Log Queries | Ability to customize the time period to query the built-in records of security attack logs, such as DoS attacks, Web attacks, IPS, virus detection, botnet/remote control Trojan detection records, website access records, system operation logs; | |
| statistical analysis | Support customized statistics of server security risk, terminal security risk, website access, web application and traffic, antivirus statistics of specified IP/user group/user/application in specified time period and form reports; | |
| Consolidated security risk statement | Provide comprehensive risk reports based on users/services, with the statistical dimensions of users and services instead of IP addresses; provide excellent, good, medium and poor ratings based on the network risk status; attack statistics provide two dimensions: the number of all detected attacks and the number of effective attacks; the report content presents the distribution of vulnerabilities from active scanning, and matches the attack logs to output the number of attacked vulnerabilities and the number of discovered vulnerabilities in the statistical reports; business The security report provides information such as attack analysis, vulnerability assessment, and business system vulnerability details; the user security report provides information such as details of the most attacked users and details of abnormally connected users; the security risk type summary is based on the type of attack on the business system, the type of the most existing vulnerabilities in the business system, and the type of the most threatened users; | |
| Summary statements | Support the generation of network data statistics summary and trend of the specified time period, the summary content including servers, hosts, statistical analysis of security events, application statistical analysis, upstream and downstream traffic statistical analysis, website access behavior analysis; | |
| Report Subscription | Support daily/weekly/monthly auto-generated reports and send the reports to the specified email address automatically, you can customize the report content; | |
| Configuration of business systems | Support for business system customization, in the report can be combined with the business system for the analysis of security threats and attacks suffered; | |
| Report Export | Support report export in Excel, PDF and other formats; |