Description
spotlightBehavioral safetySensing insider threats, making the entire network visible and controllable
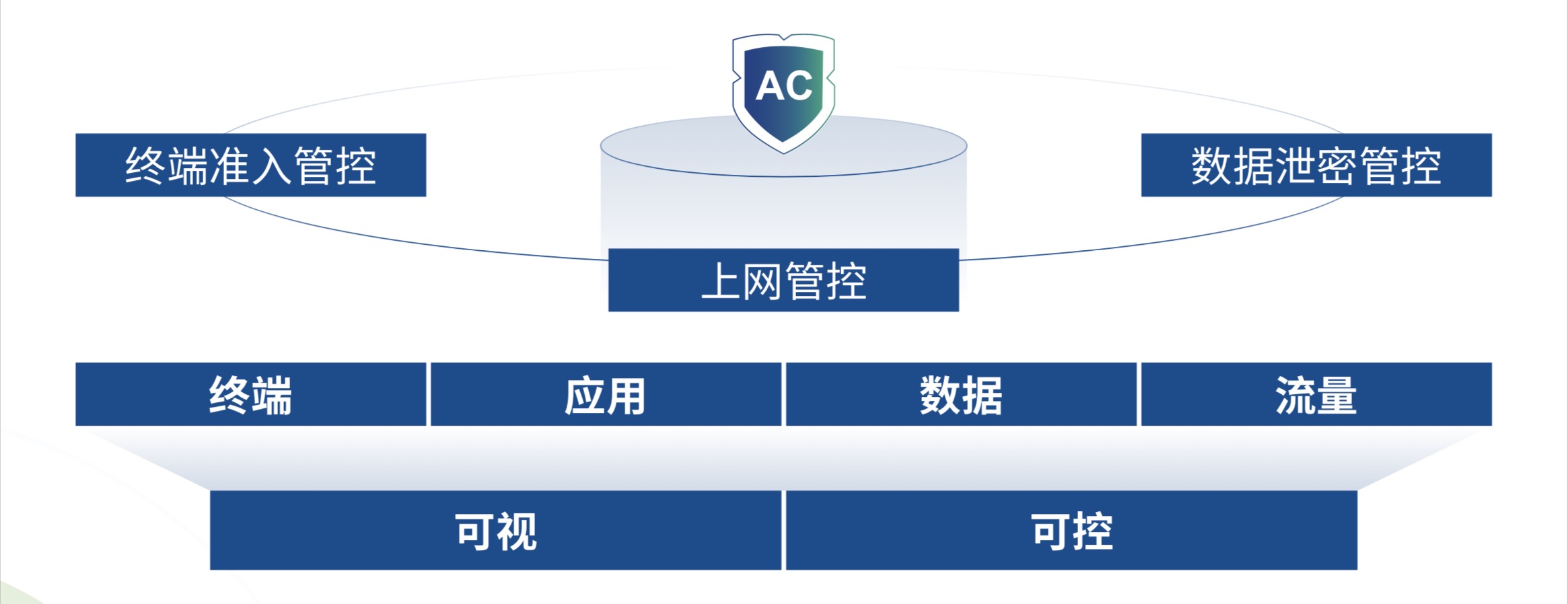
Network-wide behavioral management supports the visual control of terminals, applications, data and traffic in the whole network, intelligently senses internal risks such as terminal access violations, Internet violations and sensitive data leakage, and realizes integrated behavioral security control of terminal access control, Internet access control and data leakage control.
Products
Network-wide behavior management AC series products include network-wide AC gateway devices, internal threat management system ITM, and integrated terminal security clients. The products are capable of linkage, and through terminal access control, Internet access control, data leakage control, and internal threat perception, the complete closed-loop control program helps users to deal with the behavioral security risks of internal personnel at all stages.
Terminal access control
Establishing security norms for terminal access to the network, reducing security hazards and the risk of data leakage.
- Terminal Discovery:
Highly accurate identification of terminal types, asset sorting and classification management of access terminals (PCs, cameras, IoT terminals, etc.);
- Access Authentication:
Provides 802.1x, Portal and other methods for authentication, adapting to a variety of scenarios such as employee and visitor access;
- Security checks:
Check the security of the terminal before entering the network, including no update of operating system patches, no installation of antivirus software, etc;
Behavioral authority control is realized for the networked terminals, including USB flash drive control, anti-illegal outreach, and so on.

Safeguard online norms and online experience to avoid violations and reduce online complaints.
- Flexible flow control:
Supports dynamic flow control to give full play to the value of bandwidth and guarantee reasonable bandwidth allocation;
- Compliance Audit:
Patented SSL auditing technology is enhanced and logs are stored in accordance with the law for a comprehensive and oversight-free compliance audit;
- Fine control:
Based on the massive URL library and application rule base, it realizes application segmentation action control and accurately matches the enterprise Internet control specification;
- Behavioral Perception:
Scenario-based intelligent analysis of logs to achieve work efficiency analysis, addiction network analysis and other applications, giving full play to the value of behavioral data.
Data Leakage Control
Establish norms for data outsourcing, analyze risks and prevent sensitive data leakage.
- Outgoing control:
Support network leakage control and terminal leakage control, strictly blocking the data leakage path.
- Data Audit:
Comprehensive network auditing, business auditing, terminal auditing, data usage and distribution are clearly documented.
- Risk Analysis:
Linkage ITM realizes outgoing risk analysis and business risk analysis, and intelligently identifies and warns of data leakage.
- Leak Retrospective:
Linkage ITM realizes file similarity search, OCR image recognition and other traceability methods to meet the needs of traceability and forensics in multiple scenarios.




Reviews
There are no reviews yet.