Description
demand analysis
Michael Bobbin (Editor-in-Chief of Computer Security Magazine) says, "There's only one way to guarantee a system is truly secure: disconnect the network, and that may be becoming a real solution." Rock-solid security is especially critical in many important areas such as government, defense, and energy, where the requirements for data confidentiality, network smoothness, and business continuity are extremely high. Market demand has given rise to innovation in security technology, in the mid-1990s the Russian Ry Jones first put forward the concept of "AirGap" isolation, and then, Israel developed a successful physical isolation card, to achieve the security of isolation between the network; then, the United States Whale Communications Company and Israel SpearHead has launched the e-Gap and NetGap products, the use of proprietary hardware to achieve the two networks in the case of non-connected data security exchanges and resource sharing, so that the security isolation technology from the simple realization of the "network isolation prohibits the exchange of" development to the "security isolation and reliable, reliable, and reliable, and reliable, and reliable, and reliable". "Secure isolation and reliable, controllable exchange". According to the relevant national policies and the highest standards, our company has developed the Tianqing security isolation and information exchange system GAP-6000 series products (referred to as the network gate), which provides the most comprehensive and secure solution for the users' network isolation and security by virtue of its powerful functions, excellent performance, and perfect customer service organizations and guarantee system all over the country.
Products
Tianqing Security Isolation and Information Exchange System GAP-6000 series products are security isolation and information exchange systems with completely independent intellectual property rights of Qisda Group, relying on its strong technical advantages and years of accumulation of information security product research and development, and strictly complying with the requirements of design specifications of the relevant national authorities. The product utilizes the isolation and exchange matrix technology to realize the security isolation between two networks or application systems. The product can be deployed at the network boundary, connecting two or more networks with the same or different security levels, realizing security isolation between two or more networks without affecting the data exchange between them, thus realizing high security between networks. The product is mainly used in government, health care, energy, finance, public security, petroleum, petrochemical and other fields of information system security construction, to realize the security isolation between networks or application systems.
Functional Features
- Safe "2 + 1" system architecture, that is, "intranet hosts" + "switching isolation matrix" + "extranet hosts "to realize real security isolation;
- Secure internal and external network independent management mechanism, internal and external network using independent operating system, mutual distrust, to provide double protection;
- Intranet/extranet host-specific proprietary intellectual property operating system, solidified in hardware, tamper-proof;
- User-friendly graphical interface, secure HTTPS remote management with password and certificate authentication methods;
- High-speed security isolation chip and switching chip, double ferry transmission technology, strongly improve the performance of data exchange;
- Parallel processing, thread pooling and other technologies within the system improve the efficiency of content inspection, filtering, protocol analysis and virus scanning;
- Intelligent full-text content filtering, full-text data reduction of isolated exchange messages, in-depth detection and filtering of text content, protocol formats, etc;
- Efficient virus filtering technology, self-developed protection engine that combines eigenvalue detection and heuristic detection to efficiently filter multiple forms of viruses;
typical application
Schematic diagram of a typical deployment of the product:
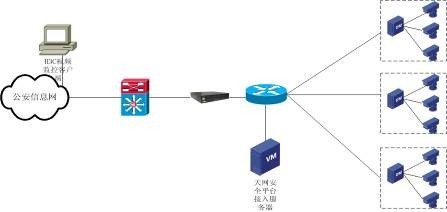
Figure 1 Public Security Video Access Deployment Diagram
Case Notes:
The product is deployed between the public security ICT network and the public security video surveillance network to ensure the security isolation between the two networks, and at the same time, through the video transmission function, it can recognize the legitimate video protocols, and effectively ferry the video images and related surveillance video signaling to the opposite end of the network.
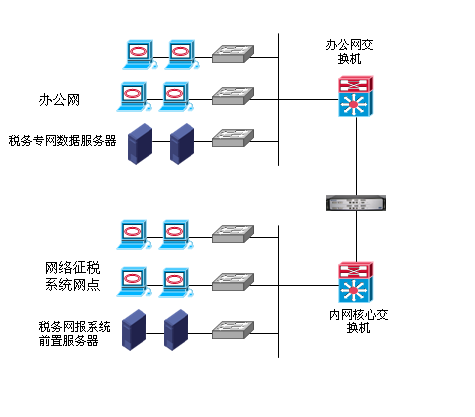
Figure 2 Schematic diagram of tax office network and intranet security isolation deployment
Case Notes:
The online electronic tax declaration system is divided into three parts at the tax end, namely, extranet acceptance platform, intranet processing platform and intranet declaration database. The product is deployed between the external network acceptance platform and the internal network processing platform. The data server of the specialized tax network can obtain useful data for preservation through the network gate, and at the same time, it also ensures the security of the internal network database and the security isolation of the external network.
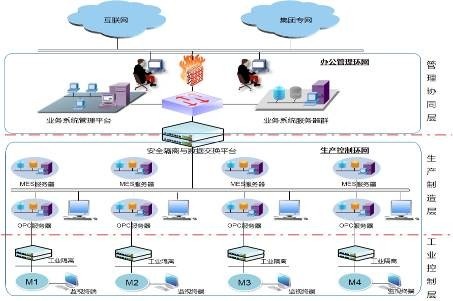
Fig. 3 Manufacturer separates the production network from the office network by means of a gate.
Case Notes:
The product is deployed between the enterprise's management network and production network, mainly used to ensure the effective isolation of the production network from other networks, while at the same time to meet the necessary data retrieval and collection of office network business. The data to be exchanged between the production network and the office network are the data in the real-time database and the monitoring video data. Through the network gate can not only meet the one-way transmission requirements of the database, but also ensure the two-way communication of the video, and the content and flow of data exchange between the two networks can also be clearly defined.
| network interface | Standard 2U chassis, dual redundant power supply; the whole machine is equipped with LCD screen and equipment health monitoring sound and light alarm device; internal network interface: standard 1 management port, 1 HA interface, 4 10/100/1000M Base-TX network interface, 4 Gigabit SFP slot, 2 10GbE SFP+ slot external network interface: standard 1 management port, 1 HA interface, 4 10/100/1000M Base-TX network interface, 4 Gigabit SFP slot, 2 10GbE SFP+ slot external network interface: standard 1 management port, 1 HA interface, 4 10/100/1000M Base-TX network interface, 4 Gigabit SFP slot, 2 10GbE SFP+ slot 1000M Base-TX network interface, 4 Gigabit SFP slots, 2 10 Gigabit SFP+ slots |
| performances | Throughput ≥ 7Gbps, maximum number of concurrent connections ≥ 350,000, delay ≤ 1ms |
| system architecture | The "2+1" system architecture, i.e., consists of two host systems and one special hardware for isolation and exchange; the isolation and exchange matrix is realized based on a special chip, which ensures that the internal and external network isolation cards are disconnected from the internal and external network systems during the time of data transfer. |
| redundancy system | Internal and external network host system respectively support dual-system boot, and can be directly configured in the WEB interface startup sequence, in the event of system A failure, you can switch to system B at any time; and support for system (including configuration) backup; support for restoring the factory version function, a key to restore the system to the factory state |
| network and interface | Supports IPV6/IPV4 dual-stack access |
| Supports interface redundancy mode settings including: polling, hot standby, link aggregation protocols | |
| Mandatory Access Control | Supports two authentication methods: WEB authentication method and dedicated client (user authentication client). |
| Access control by checking the user's client version and process | |
| Optional Function Modules | Database synchronization, file synchronization, FTP synchronization, email transmission, secure browsing, video transmission, etc. |



Reviews
There are no reviews yet.